
There's a new trend of online services doing away with passwords and simply requiring a user to click on a link sent to them in an e-mail to their registered address.
Depending on your audience, this technique may well be considered more secure than simply asking users to choose a password. A password that they likely use on all their other services and/or is just the name of their dog.
Monzo just published an article about how safe they are. On the whole, I love Monzo and what they're doing but this article made me think about their login process in more detail and whether I was comfortable with it.
When you're a bank and you have vast amounts of sensitive data at your fingertips, you need to think twice about employing the "magic login link" technique without any form of secondary authentication.
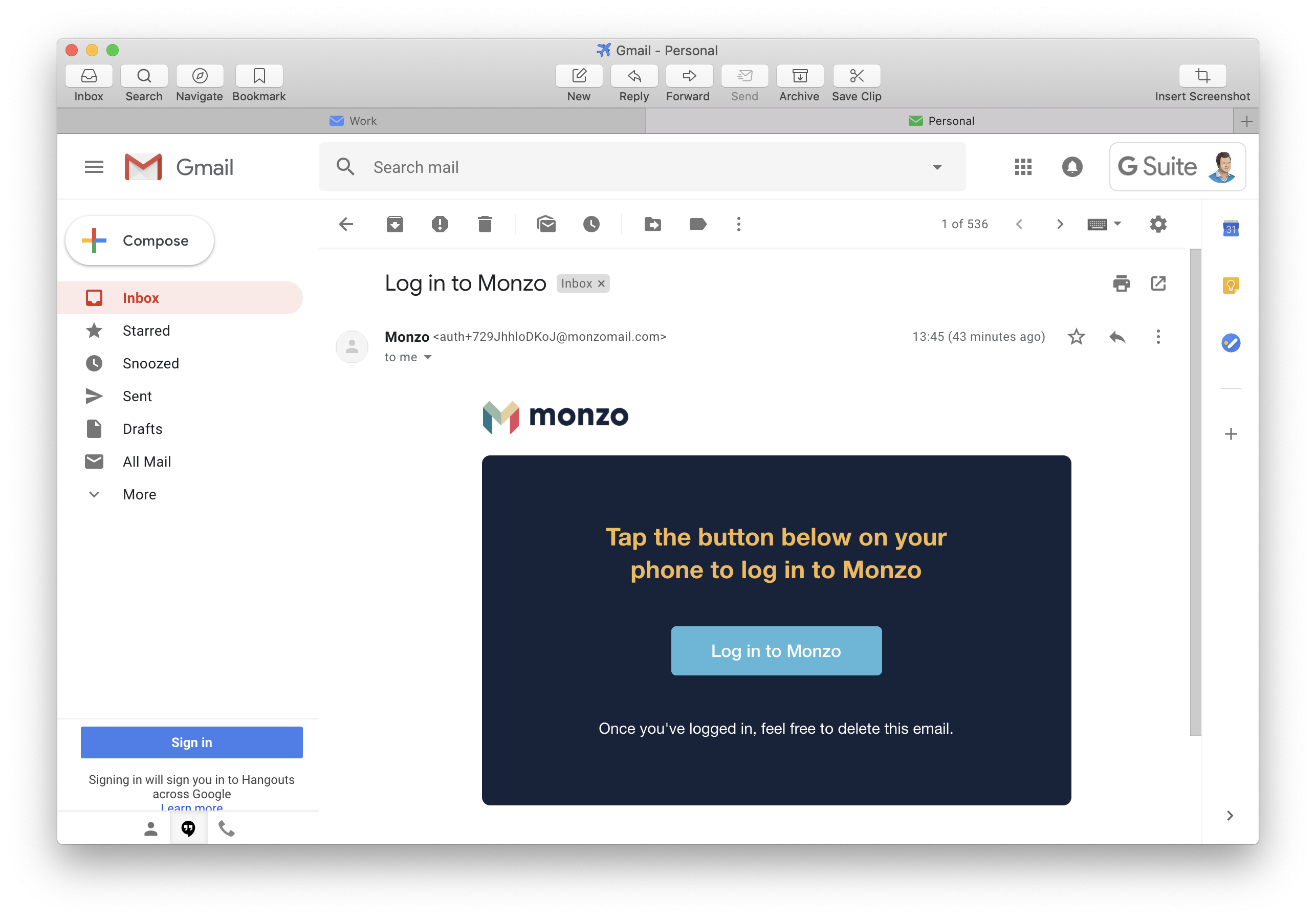
There is a claim that your account is protected because of your phone's biometrics - fingerprint or face ID. While this protects access to your phone, it does absolutely nothing to protect access to your data at Monzo. All that is needed to login to your Monzo account (either from their mobile apps, their web interface or through IFTTT) is access to your inbox.
People say that you simply need to add another factor of authentication to your e-mail account to protect your account. While this will add some additional security to your account, it is by no means fool-proof as an attacker does not necessarily even need to login to your inbox.
- Many people still do not understand two factor authentication and leave their e-mail account without it enabled. Work is certainly being done to help improve this situation but we're not there yet.
- E-mail is still commonly transmitted insecurely between mail servers. It seems that Monzo do support sending e-mail securely and if the receiving provider supports it it will be transmitted to them securely. There's no guarantee that it won't be passed around insecurely on the provider's own network though!
- Your e-mail provider (and their employees) can potentially just access your inbox without any authentication. They'll just look at the files on their server or in their database. The most popular control panel for shared hosting, by default, just stores your e-mail in plain text on a shared server.
- While big providers allow you to set up two factor authentication, many smaller ones may only do this for webmail logins or not at all. IMAP is frequently left only secured by a username & password.
- Your inbox is easily accessible on an unlocked and unattended computer and/or phone. Unlike a password manager, your inbox doesn't lock itself after some inactivity.
Why would a bank want to entrust the security of their customers to a completely unknown third party? The bank has no idea who they're sending that login link to and what procedures they have in place to protect the sensitive data they're sending them.
Having said all that, there are some mitigating factors.
- The login link only works once. An attacker would need to request one, and use it quickly before you had an opportunity to use it yourself. This isn't a huge leap to expect someone to be able to do this though.
- Money transfer actions are protected by a second factor of authentication. I haven't actually checked that the API enforces this or whether it's just the phone but I assume it's the API. However, all data stored by your bank should be protected and is sensitive. Other companies have started to use information from your credit report to verify your identity and this information can, potentially, be obtained from just looking at your bank statement - your mortgage amounts, regular bills, associated people, etc...
- For some users, a magic link still may prove to be more secure than simply asking them to choose a password.
What do I think needs to happen? There should always be a second factor of authentication by default when logging into your account. Keep the magic link but it must be combined with a requirement for something that I know or something else I can access. This is not a simple thing to solve.
- Many banks require users to use card readers or external security code generators to login to their account. I'd imagine Monzo very much want to avoid this and I, personally, hate the idea of it.
- Send a text? Widely considered as insecure as e-mail and a problem if you lose your phone.
- Send a push notification to your registered phone the same way as 3D Secure payments are authorised? A good option but useless if you lose your phone.
- Dynamic security questions about recent activity on your account may be an option to consider for users who lose their phone. "Which of these shops do you shop at the most frequently?", "When did you last shop at Tesco?", "How much did you last spend at Amazon?", perhaps? This, of course, should be combined with access to your e-mail account and perhaps combined with access to your mobile number and/or home address.
With Monzo, logging into your account is not done very often. Once you've logged in on your phone, you're good to go and your account remains protected by biometrics on your phone. While simplicity is the order of the day, does something so important that happens so infrequently really need to be so easy at the expense of some additional security?
In conclusion, magic login links leave the security of your customer's data in the hands of a totally unknown third party which I don't think anyone would normally do.
Some other recent posts

My development environment
In this video I'm taking a quick look at my development environment. Looking at code editor, terminal, databases, containers, web servers and more.

A quick intro to service classes
To get things started, in this video I'm looking at how service classes are used in the application. Service classes form the basis for much of the logic within this app so it's a good place to start

I'm building an app hosting platform
I'm building a app hosting platform and in this video I'm going to introduce you to the project and show you what I've got so far.

